AI-Powered Intelligence
AI Agents for Cyber
Threat Hunting
Agents tirelessly answer questions, investigate alerts, and proactively hunt for
threats—keeping your enterprise secure.
Empower Security Teams Through Intelligent Automation
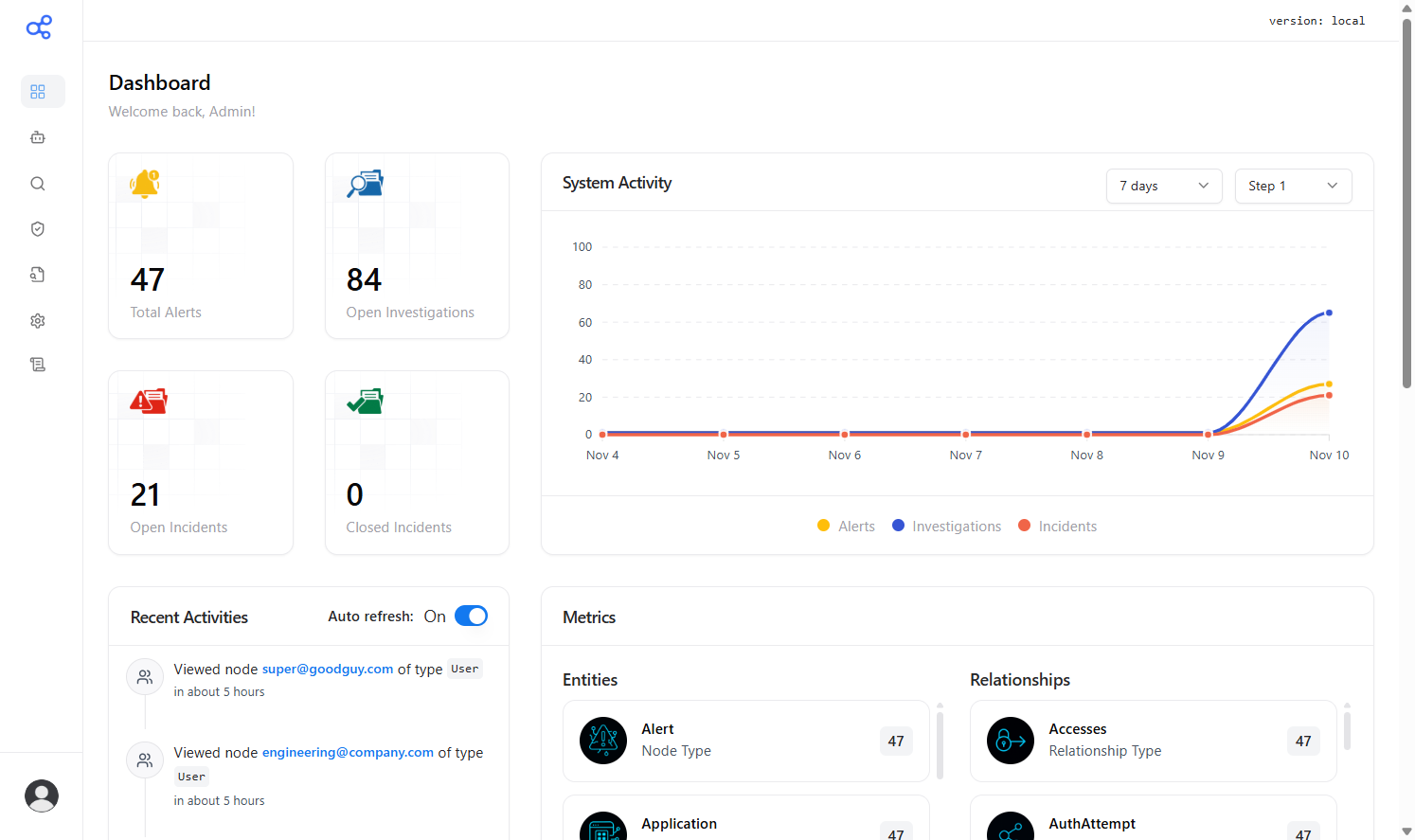
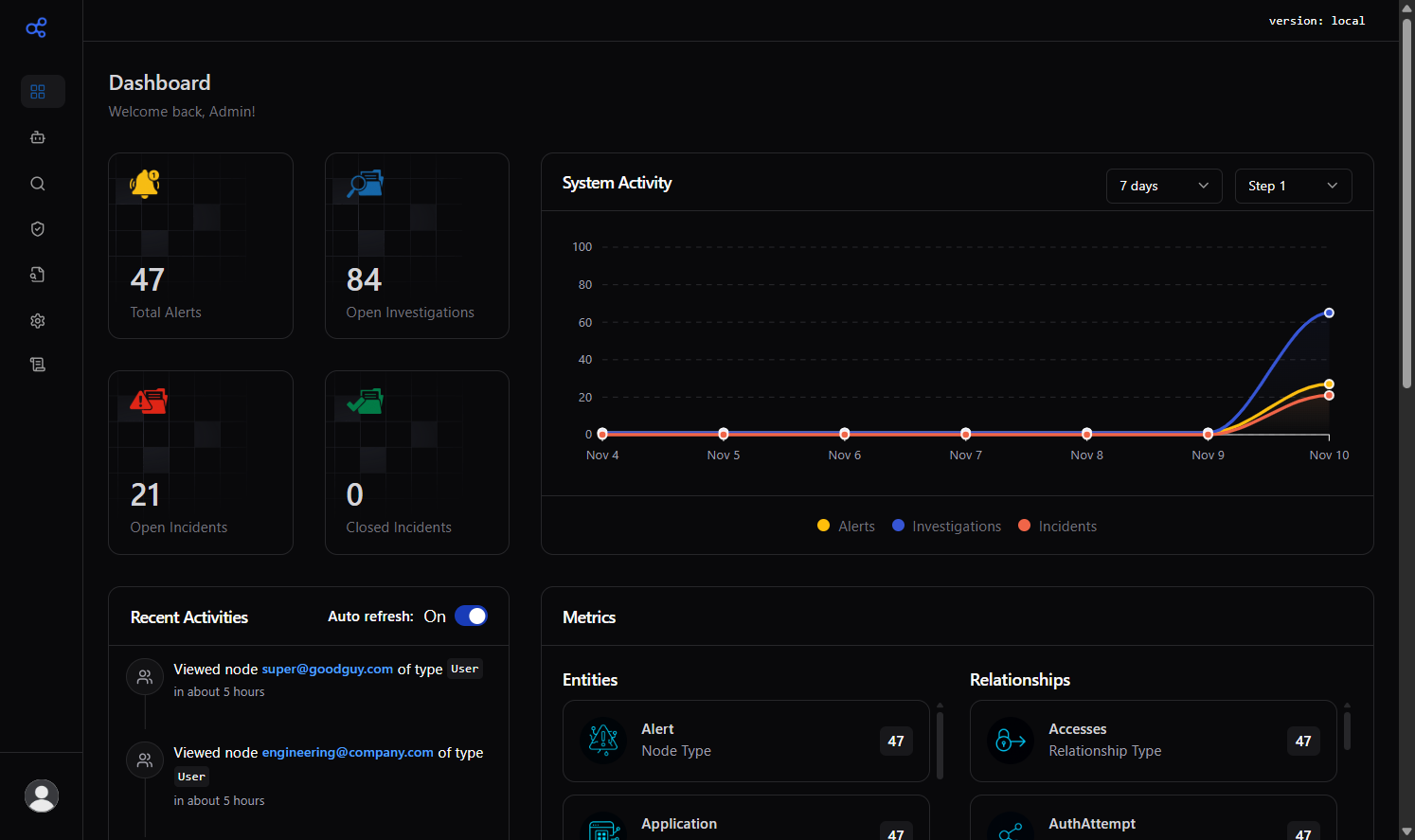
Use the slider to compare the dashboard in dark and light mode. Drag or use the keyboard arrow keys to move the divider.
Our services
Get answers fast
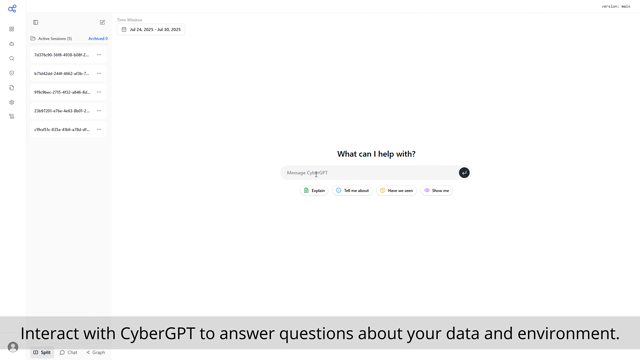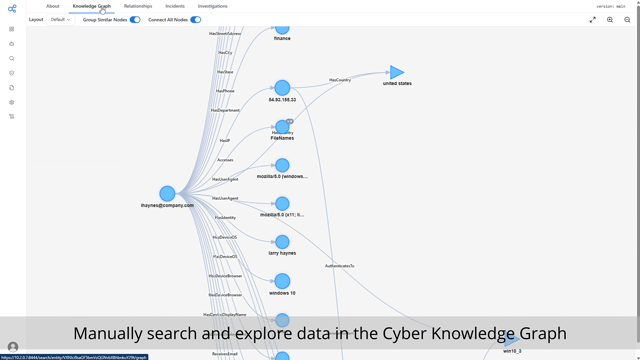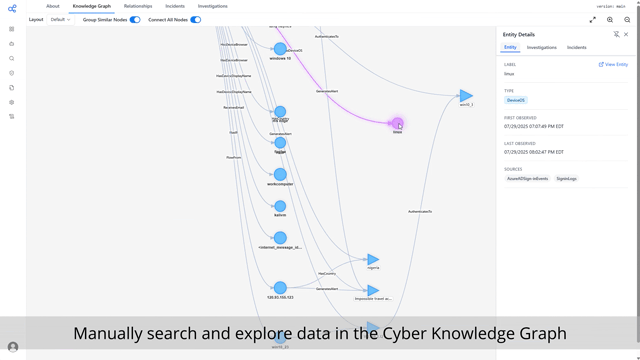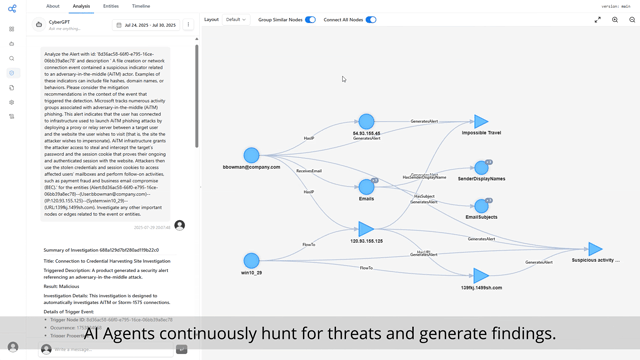
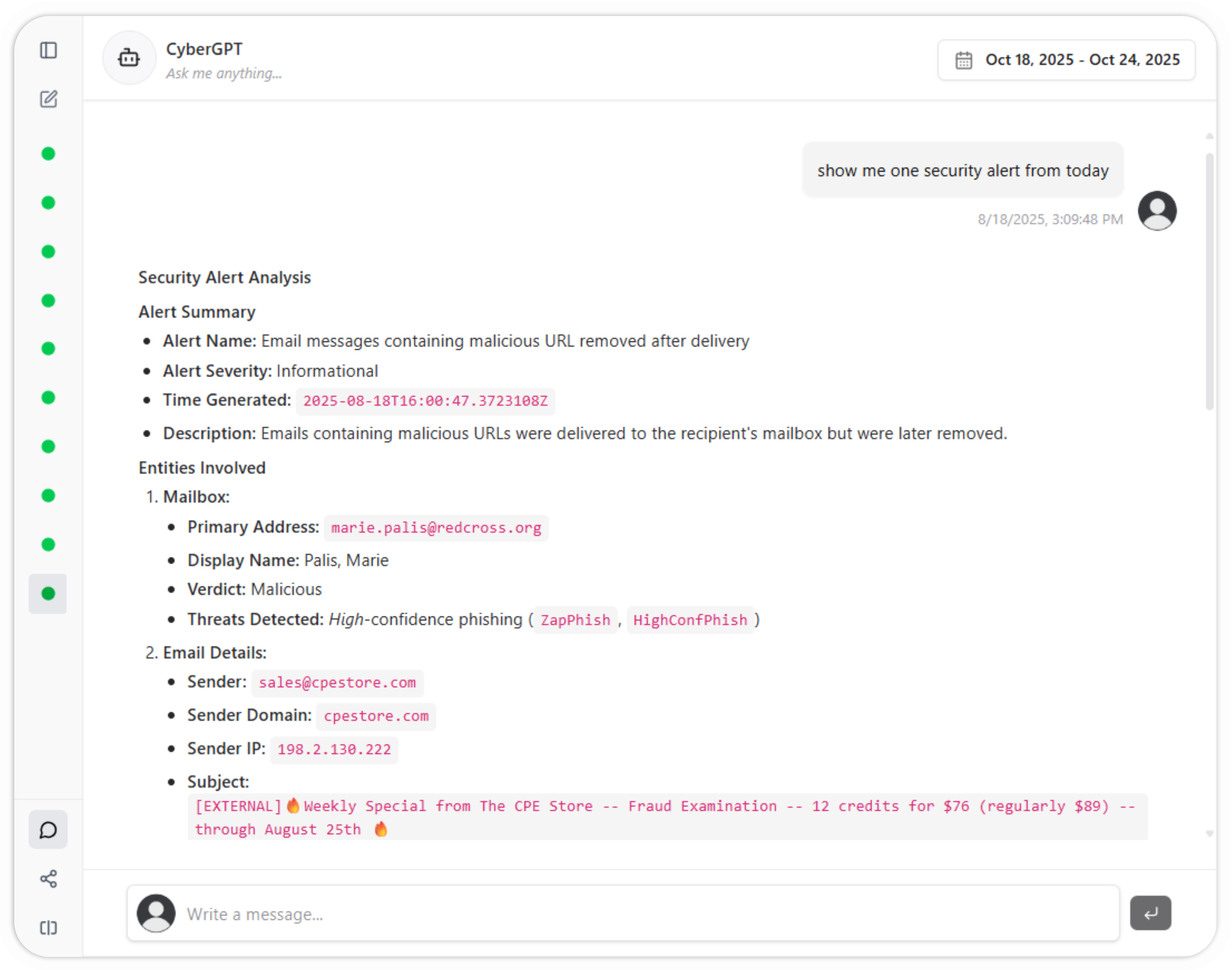
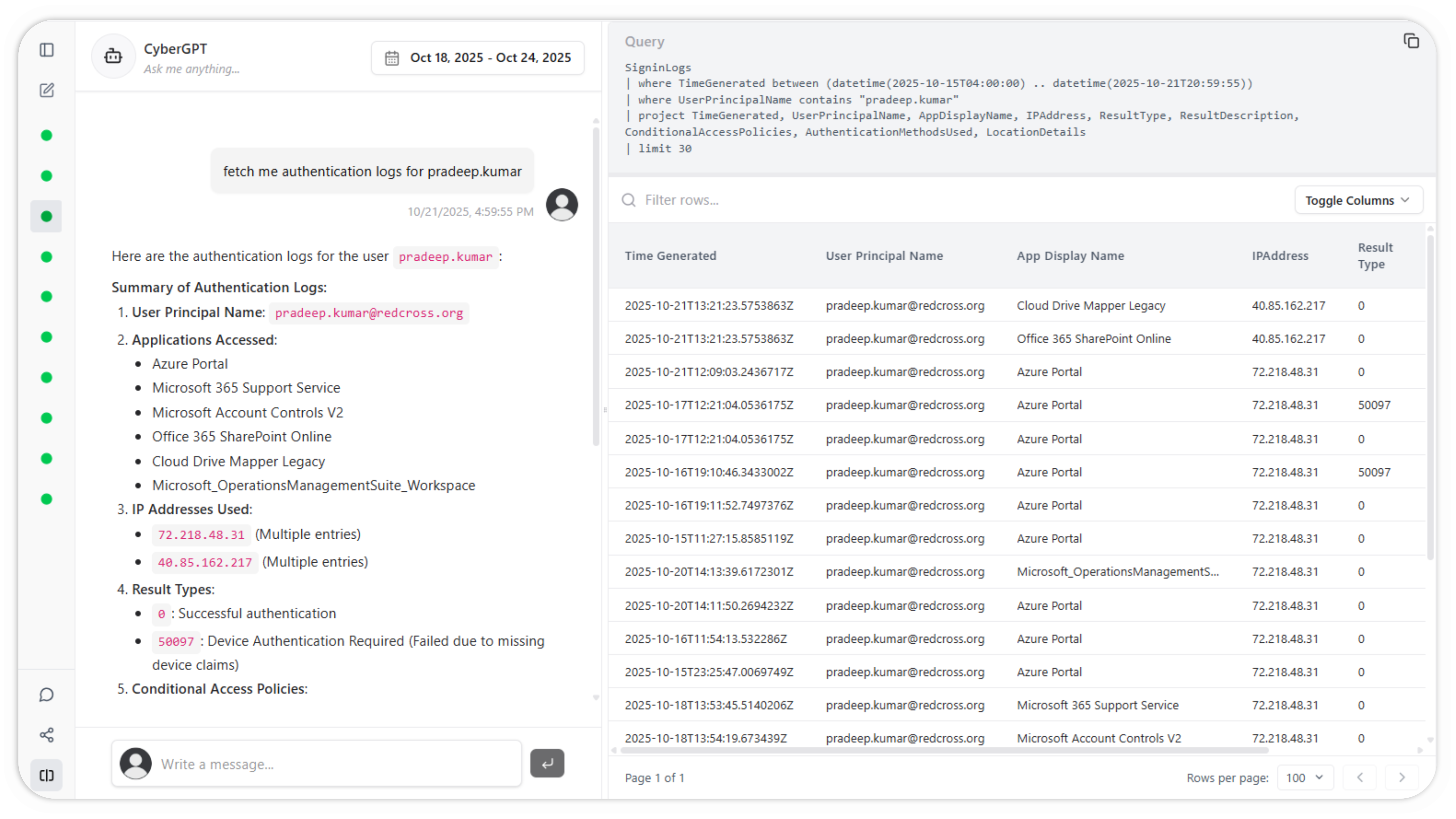
Cybersecurity operations is a never-ending process of answering questions - "Who logged into that machine?", "What system has that IP?", "Who sent that email?". Cyber teams lose hours to days of time constantly hunting down these answers.
With Cybermonic, getting answers to your questions based on all of your data sources is as simple as asking the question.
Investigate every alert
Analysts are constantly racing to keep up with the onslaught of cybersecurity alerts from all of their tools, typically only able to analyze and investigate a subset of the valuable alerts generated by their curated set of tools.
With Cybermonic, an AI analyst will happily investigate any and all of your cybersecurity alerts. You can provide with specific playbooks, or let it use its internal cybersecurity intuition to best defend your network.
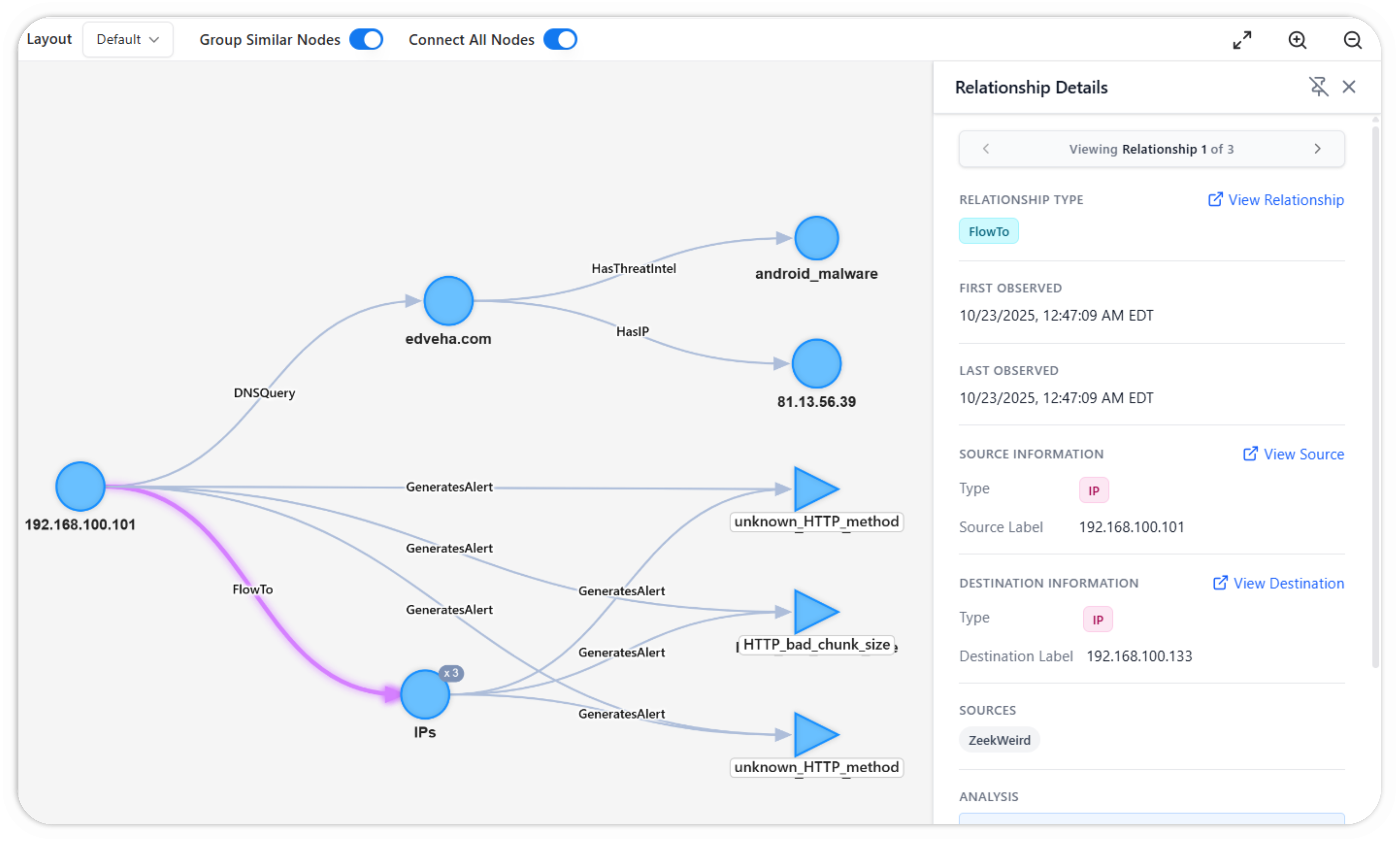
Threat Hunting for all
Threat hunting is often a process reserved for only the most sophisticated cybersecurity programs, despite the fact that their are malicious cyber actors targeting organizations of all sizes.
With Cybermonic, any organization can have an effective threat hunting process. The Cybermonic Threat Hunting AI agent will reason about your organization, emerging threats, and look for relevant indicators of compromise in your environment.
What our clients say

Enterprise
Cybersecurity Analyst
A New Era of Cybersecurity
The security of an organization is no longer dependent on the headcount of their SOC, or the expertise of their analysts. With Cybermonic, unleash the power of AI for your security operations.
- Query your security data using natural language
- Investigate seamlessly with Split, Chat, and Graph layouts
- Maintain active sessions with independent time windows
- Get explainable answers with full references and audit trails
How does it work?

Connect your tools and data
Point Cybermonic at any data source or cybersecurity tool. Our Agentic AI framework will understand how and when to use these capabilities.
- SIEM / Log Aggregators / Data Lake
- Endpoint Tools
- Network Tools

Enable your AI agents
Cybermonic has a variety of agents ranging from simple copilot agents to help you understand your log data better, to fully autonomous threat hunters and incident responders. Choose the agents that fit your use case.
- SIEM Answer Engine
- Alert Investigation Support
- Threat Hunting

Ask & Act
Interact with your agents directly, asking questions in natural language. Agents can present findings and recommendations to analysts for actioning, or can act in a fully autonomous mode.
- Natural Language Questions
- Recommendations
- Automated Responses
Get Started with Cybermonic
Discover how Cybermonic can enhance your security operations.
Schedule a demo